
By John Macario, SVP of Product Management and Marketing at Edgewater Networks
The beginning of a new year is a time when many business managers reflect on learnings from the previous year and begin working on their goals for the current year. Business continuity and data security are, of course, top priorities and securing the network is a vital part of this.
For network professionals, there is no word more fearsome than “breach.” A security breakdown can mean lost data, stolen secrets, expensive lawsuits, and more. According to IBM, the average cost of a data breach is now US$4 million. This is why nearly every organization that knows what's good for it now invests in antivirus, data loss prevention (DLP), and of course, firewalls.
These days, however, we need to protect more than just data. Enterprise communications have grown into a multi-billion dollar market, particularly due to the widespread adoption of VoIP and unified communications (UC) services. This presents a new challenge that firms will have to face in order to gain a winning edge: voice security. IP phone services present a whole new attack area to potential hackers, a frontier that firewalls simply cannot protect by themselves. The essence of this challenge lies in the fact that we're talking about two entirely different types of information transmission that, in turn, require different security solutions.
Distinguishing between two types of traffic
Data is transmitted in packets, or “frames,” with each one containing the addresses from which the information is sent and received. When threats emerge, firewalls identify and quarantine a select range of data packets before bringing the full force of its security tools to bear. Digital voice traffic doesn't work this way — once the circuit (voice call) is established, no further address information is exchanged until the call ends (termination of the circuit). No packets are transmitted in this scenario. In essence, these two types of traffic are speaking in different languages. It would be a major coup for network professionals if these two mutually unintelligible languages could be reconciled and administered in a uniform manner. But that point of voice and data evolution has not yet occurred.
Fortunately, this not to say that voice security isn't achievable today: intelligent edge solutions, particularly through the use of enterprise session border controllers (eSBCs), are fully capable of securing voice traffic. While firewalls are able to approve or deny access to certain callers or call recipients based on established parameters, intelligent edge systems monitor voice sessions as a whole, and in real time. No packets? No problem. That means the ability to cut out DoS (denial of service) threats without interrupting network traffic. Conversely, reconfiguring firewall protocols on the fly can be disruptive to IP communications services.
As VoIP and UC adoption expands and their offerings become more diverse, the essential need for intelligent edge solutions increases in lockstep. In addition to security, there are two main benefits offered by eSBCs that firewalls cannot match: interoperability and quality assurance. To get a handle on why this is, we need to talk about layers.
Where do voice calls fit in the OSI model? 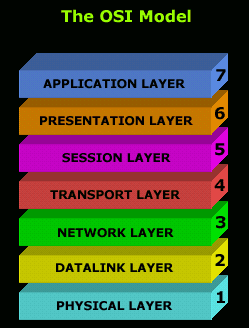
The OSI model consists of seven layers which all need to be administered in unison for enterprise communications to function as intended. The problem with firewalls by themselves is that they only address layers 3 (networking) and 4 (transport) without touching layer 5 (session). Modern workplace communications, from security to call quality, depend on coherence among all three. With no control over the session layer – the one concerned with network apps like video conferencing – QoS (quality of service) cannot be assured. Intelligent edge solutions avoid these issues altogether by working in concert with a firewall: depending on the nature of the problem, eSBCs can permit firewalls to police network threats, but when the session layer comes into play, intelligent edges address the danger while avoiding disruptions in service.
CONCLUSION
Firewalls were designed to address security first, with potential collateral impacts on network functionality taking a bit of a back seat. The brilliance of intelligent edge solutions lies in the fact that firms no longer have to choose between the two.
If you're ready for life on the edge, and would like to learn more about how Edgewater Networks Intelligent Edge solutions can secure your enterprise UC deployment, check out our white paper: Firewalls vs. SBCs: Understanding the OSI Stack Model and Implications for RTC.
Browse TeleDynamics' website for Edgewater Networks eSBCs.
You may also like:
Five reasons you should add an eSBC to your IP network
Is your SIP phone system safe?
Wi-Fi network security: Do you have a blind spot?








Comments