Hybrid and remote work have redefined the modern workplace. Teams now connect from headquarters, branch offices, home networks, coffee shops, and even while traveling — often switching between Wi-Fi, broadband, 5G, or satellite links in the process. With so many moving parts, keeping voice and video calls consistently clear can feel like an uphill battle. Dropped audio, frozen video, and lagging meetings are not only annoying, but they can be costly in terms of eroded productivity and hampered user experience.
This is where SD-WAN makes a difference. By intelligently orchestrating multiple types of connections, SD-WAN can turn this patchwork of networks into a reliable platform for communication. In this article, we’ll show you how SD-WAN helps overcome the pitfalls of underlay diversity, which mistakes to avoid when deploying it, and the best practices that ensure your UCaaS quality remains high. By the end of the article, you’ll be better equipped to assess your network strategy and support seamless collaboration no matter where your teams are working from.
Read More
Topics:
QoS,
Network Security,
Network Design,
SD-WAN,
UCaaS
One device, endless capabilities: Grandstream’s GCC6020 series brings together communications, security, VPN connectivity, and switching into a single, compact solution that seems almost unbelievable — until you see it in action.
This appliance combines an IP PBX, firewall, VPN router and network switch into one sleek platform. In this article, we examine the GCC6020 series and highlight its compelling characteristics for both small and mid-sized businesses. Read on to see how these devices make enterprise-grade performance easier and more affordable than ever.
Read More
Topics:
IP PBX,
QoS,
Total Voice Solution,
Grandstream,
Network Security,
Product Review,
Switches,
Unified Communications,
Firewall
Over the past 20 years, Grandstream has made a name for itself by providing specially designed IP telephony solutions for small and medium-sized businesses. The company has since expanded its portfolio, adding a comprehensive suite of networking products and solutions.
In this article, we showcase Grandstream's telecom and networking portfolio and how it offers a comprehensive network solution for virtually any SMB.
Read More
Topics:
Grandstream,
Network Security,
Videoconferencing,
Gateway,
Wi-Fi,
Switches,
Unified Communications,
Facility Management,
Network Infrastructure
When looking at telecom equipment or reviewing datasheets, you likely have noticed some cryptic symbols or acronyms followed by words like “certification” or “compliant.” But what do they actually mean?
Most people skim over these designations, preferring to focus only on the seemingly more important technical information. However, the truth is that these specifications are just as important as performance specs, protocol support, and device capabilities.
In this article, we look deeper at these certifications, what each one means, the organizations that define them, and why they are important aspects to consider when choosing telecom equipment.
Read More
Topics:
Network Security,
Unified Communications,
Regulations,
Communication,
Network Infrastructure
Artificial intelligence (AI) continues to dominate tech headlines, affecting many industries due to its incredible potential. Network infrastructure is one area where AI’s ever-improving technology has a significant impact.
In this article, we examine how AI-driven network infrastructure works to help you understand how AI and related tools influence network design, maintenance, and management. We also explore related principles specific to voice, video, and unified communications (UC), highlighting how AI-enabled infrastructure enhances these essential services.
Read More
Topics:
Network Security,
Network Design,
Unified Communications,
AI,
Network Infrastructure
Network services such as voice over Internet Protocol (VoIP), unified communications (UC), video conferencing, and collaboration systems are fundamentally dependent on the quality and robustness of the underlying network infrastructure. When deploying an enterprise network, it is crucial to implement sound network design principles to guarantee optimal performance, reliability, and scalability.
Various aspects of enterprise network design work together to achieve high levels of network performance. This article focuses specifically on quality of service (QoS) and some best practices associated with it.
Read More
Topics:
QoS,
VoIP,
Network Security,
Network Design,
Unified Communications
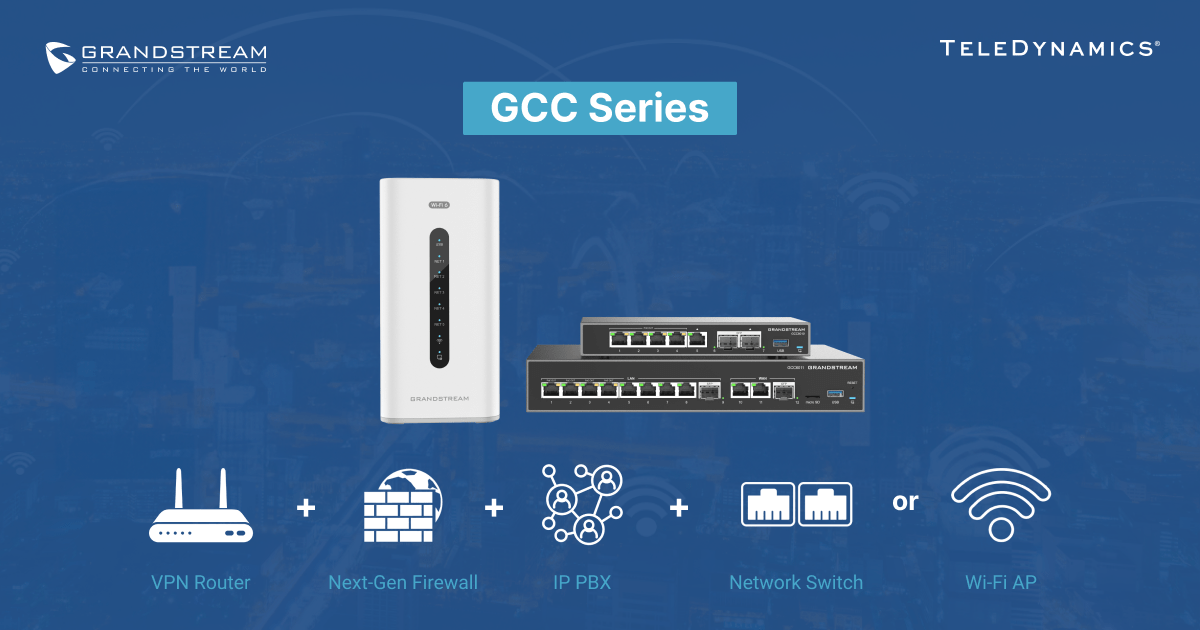
Grandstream’s latest GCC Series of unified communications (UC) and networking convergence solutions offers a range of devices that deliver services, network connectivity, and security features all within one compact and cost-effective unit.
In this article, we review these devices and the capabilities they offer small to medium-sized businesses.
Read More
Topics:
IP PBX,
Grandstream,
Network Security,
Network Design,
Wi-Fi,
Switches,
Unified Communications,
WAN Technology
By Brian Van Meter at Grandstream
Grandstream's portfolio of networking devices has grown rapidly over the past few years. This trend will only continue with our introduction of more switches, routers, and Wi-Fi access points.
While our Wi-Fi access points have built-in controllers that can be used to manage a deployment of APs, a more robust platform solution for configuration, management, and troubleshooting of network infrastructure is often a better choice.
Grandstream's GWN.Cloud and Grandstream Manager are just this. GWN.Cloud and GWN Manager are free, enterprise-grade management platforms for Grandstream access points, routers, and switches. Thanks to streamlined monitoring and maintenance, managing a network or several networks across multiple locations has never been easier.
Within this blog post, we'll be providing an introduction to GWN.Cloud and GWN Manager and how to use them. By reading it, you'll learn about:
- The features and capabilities of the GWN management platforms
- How to add and configure devices with GWN.Cloud and GWN Manager
- The steps to configure your network settings and options
Read More
Topics:
Grandstream,
Network Security,
Network Design,
Wi-Fi
Security is an indispensable element of business communications systems, and Yeastar's telephony security features meet the elevated standards established by industry leaders.
In this article, we delve into various common attack vectors that now target telephony systems and showcase the significant security capabilities of Yeastar's P-Series IP PBX and P-Series Cloud Edition to deal with such issues.
Read More
Topics:
IP PBX,
VoIP,
Network Security,
Yeastar,
UCaaS
The network edge is the portion of an enterprise network that interfaces with the public internet via an internet service provider (ISP). Various security measures are typically applied at this network location to protect internal network infrastructure and assets from potential external malicious attacks.
These measures may introduce challenges to the mobile workforce, especially when the unified communications (UC) and VoIP services those individuals leverage exist within the physical enterprise network.
This article examines some of the most common network edge issues that may present challenges to a mobile workforce and some strategies to alleviate them.
Read More
Topics:
Network Security,
Network Design,
Cloud,
Unified Communications





.jpg)