
The network edge is the portion of an enterprise network that interfaces with the public internet via an internet service provider (ISP). Various security measures are typically applied at this network location to protect internal network infrastructure and assets from potential external malicious attacks.
These measures may introduce challenges to the mobile workforce, especially when the unified communications (UC) and VoIP services those individuals leverage exist within the physical enterprise network.
This article examines some of the most common network edge issues that may present challenges to a mobile workforce and some strategies to alleviate them.
Securing the network edge
The term “network edge” refers to where the enterprise network connects to the broader internet. The edge typically comprises one or more devices that the enterprise owns and administers, such as firewalls and routers.
These devices are configured with security policies designed to protect internal users and services from potentially malicious attacks from the internet while enabling controlled access to the internet by those same internal users.
An effective network edge security policy and approach hinges on achieving an optimal balance between restriction and permissiveness to ensure security and functionality. Overly stringent policies can inadvertently obstruct or filter out services, while excessively lenient ones may fail to provide adequate protection.
Typical problems with UC and VoIP
UC and VoIP services operate using two distinct communication sessions. The first is the actual media transfer, be it audio or video. The second is the signaling involved in setting up, maintaining and tearing down those media sessions.
Because of this two-fold communications process, security at the network edge can interfere with one or more of these data streams in either one direction or both, especially when networks use the SIP protocol. This can result in problems such as these:
- One-way or no-way voice, where a session has been established, but one or both participants cannot hear each other in a voice-only call. Similar phenomena may be observed in the video component of communications as well.
- Blocked signaling, resulting in a failure to establish a communications session or a failure in a client registering to the IP PBX.
Why does the edge matter?
In the topology shown in the following diagram, we have an IP PBX located within the enterprise network, two internal IP phones, two mobile workers (one with a smartphone and one with a laptop), and a single phone on the PSTN using conventional telephony.
We can assume that the IP PBX has created some SIP trunks with an internet telephony service provider (ITSP).
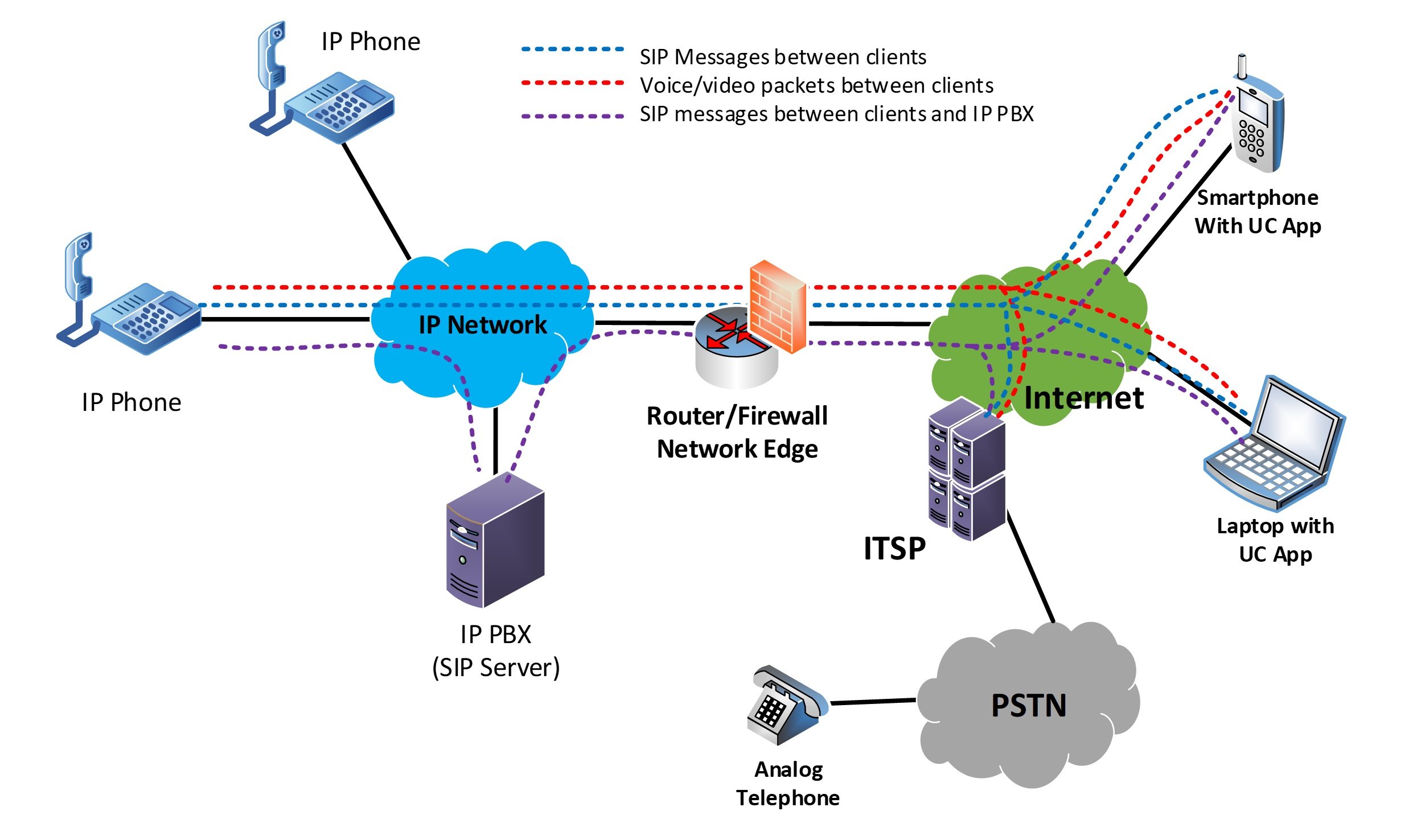
Looking at this diagram and imagining the various interactions among the entities involved, you can begin to understand that multiple data streams of various types will traverse the network edge. For example:
- SIP protocol exchanges among IP phones, the IP PBX, the ITSP, and the mobile employees due to the registration of the UC app with the IP PBX and the exchange of signaling information for calls in progress
- Audio and video streams among the IP phones, the mobile employees, and the PSTN interface of the ITSP
- For advanced features, additional streams of data traversing the network edge in certain situations, including:
- Conference calling, where the IP PBX acts as the conference hub
- Videoconferencing, where the IP PBX acts as the multipoint control unit (MCU)
- Contact center applications with music on hold, call queuing, and business application integrations
- Collaboration applications where additional data is exchanged, such as shared whiteboards, annotations, shared screens, and multiple camera angles
What may block UC apps?
VoIP and UC systems can be sensitive to various network security features applied at the network edge and can interfere with their operation, affecting call quality and reliability. Here are some of the key factors:
- Network Address Translation (NAT): NAT is often deployed at the network edge, especially when using the private IPv4 address space within the enterprise network. Careless NAT configurations can interfere with VoIP and UC traffic, resulting in blocked or altered packets, call failures, or quality issues.
- Firewall policies: These policies will typically block specific Transport Layer ports and allow others. However, VoIP and UC often use dynamic TCP port numbers, so firewalls must be smart enough to open and close appropriate ports dynamically.
- ISP throttling or filtering: Some ISPs may throttle certain types of traffic, including VoIP and UC video, which can lead to reduced call quality or dropped calls.
- VPN interference: While VPNs are useful for secure communications, they can introduce latency and packet loss, which may negatively impact VoIP and UC quality.
Solutions to the problem
Enterprises should consider several approaches when dealing with the network edge. You can deal with NAT issues by ensuring that features such as NAT traversal are properly configured on the edge equipment for UC and VoIP applications.
NAT traversal is a feature in routers and firewalls that allows network traffic to cross a NAT device in a way that does not disrupt its end-to-end connectivity.
Firewalls should employ dynamic security policies such as deep packet inspection and filtering, allowing them to actively identify the type of traffic the packet carries. Rather than using static port assignments, firewalls identify and allow all VoIP and UC traffic while denying other types of traffic.
Communicating with your ISP and letting them know the nature of the traffic they will be relaying is also essential in ensuring proper network edge operation. Informing them of the use of UC and VoIP by remote employees will safeguard against their use of mechanisms that may adversely affect your applications.
Cloud-based UC systems
The ultimate solution to resolving edge-related issues with UC and VoIP for your remote workforce is eliminating the network edge altogether. By employing a cloud-based VoIP or UC service, all communication in your mobile workforce will occur directly within the cloud and will not need to traverse your network edge. Notice how fewer traffic streams cross the network edge in the following diagram:
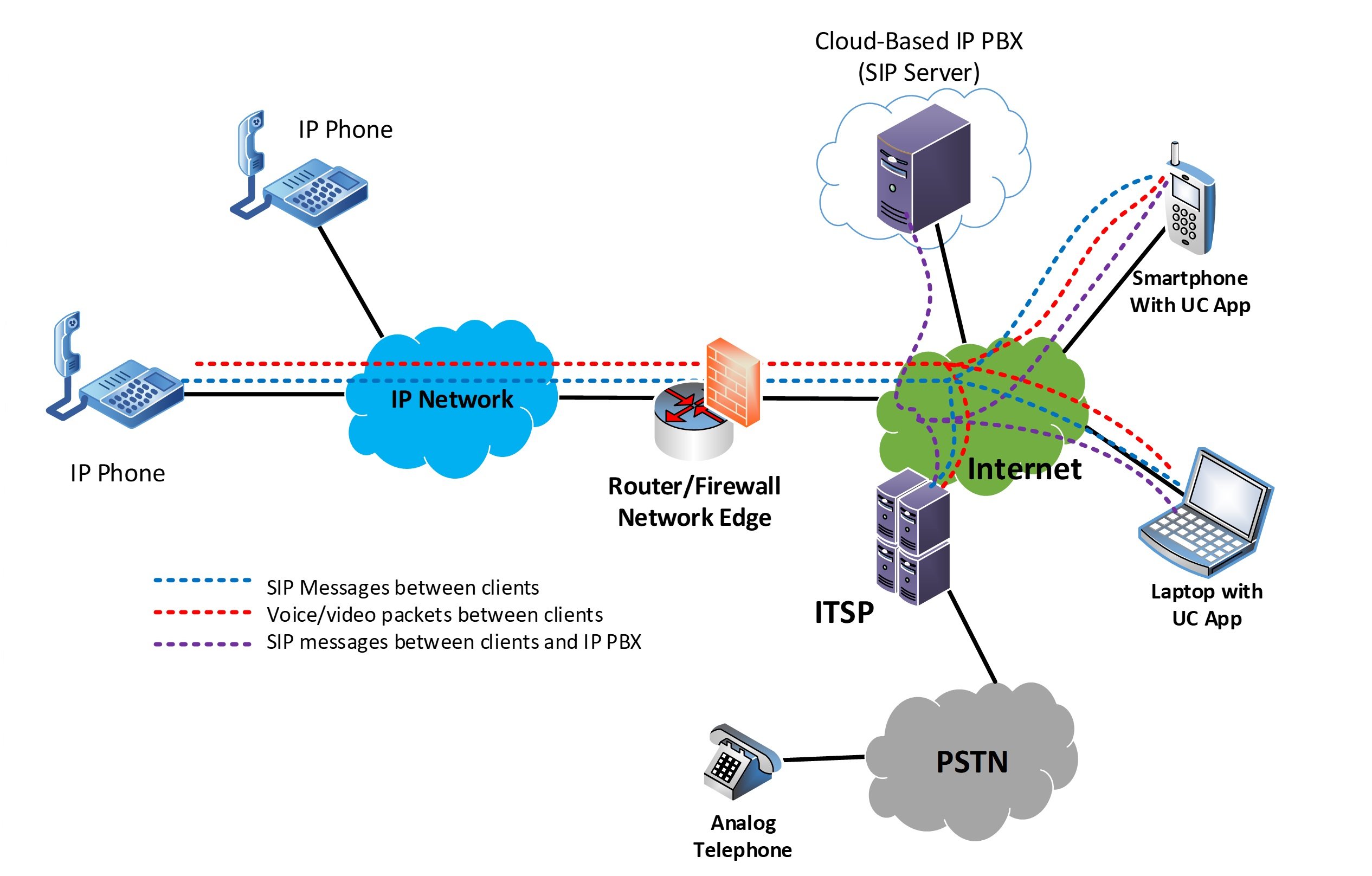
This obviously doesn’t eliminate all traffic streams traveling through the network edge, but it does simplify the process to a degree that makes problems no longer challenging to resolve. It eliminates the need for VPNs or specialized configurations to allow external users to access internal services.
Conclusion
Understanding the potential problems at the network edge for use with UC and VoIP systems is an important step in dealing with and resolving such issues. The choice of solution depends upon the approach and philosophy of each organization.
If the UC service is hosted internally on an appliance or a local data center, then the appropriate configurations must be applied at the network edge. If using a cloud-based system is preferable, such a solution resolves the edge issues altogether.
In each case, enterprises must weigh the advantages and disadvantages.
You may also like:
Zero trust security model: a paradigm shift in network security
Voice network security and troubleshooting
Network security policy best practices










Comments