Networks continuously change, and new approaches to security are constantly emerging. One particularly noteworthy approach to network security that has been increasing in adoption over the past couple of years is the zero trust security model.
In this article, we examine what zero trust is, how companies could deploy it over the next few years, and its impact on unified communications applications such as voice, video and collaboration.
Traditional security models
Conventional security measures for enterprise networks primarily focus on creating a secure network edge and establishing an appropriately protected network perimeter. This approach is sufficient for traditional enterprise networks typically located within one or more physical buildings.
In the classical arrangement, employees work within those buildings at their desks, using computers, telephones and other communications infrastructure.
The organization's data center is also customarily housed within the same location. There is a single connection to the internet and the public switched telephone network (PSTN) for computer and telephony communications with the outside world.
Security is primarily employed at the network edge using firewalls, an intrusion detection system, and other mechanisms, ensuring that everything "inside" is safe and protected from the dangers that lurk "outside" the enterprise network.
A virtual private network (VPN) is typically used by the few employees who work remotely and require access to internal resources, securely connecting these individuals to the inside network.
The evolving network
Focusing on securing the network edge and delivering a strong perimeter defense makes sense with a traditional network infrastructure. However, modern businesses have been evolving for years, and networks are growing with them.
Brick-and-mortar physical locations no longer confine companies, and the adoption of cloud computing, edge computing, and remote work continues to grow.
For example, some enterprise services may be housed on the premises, while others are cloud hosted. Some services may be delivered within a SaaS model, while others are self-hosted. Likewise, companies may store data dispersedly in on-site repositories and in the cloud.
Companies may adopt a hybrid approach to work, enabling employees to work from home, on the go, in remote offices and on site. In these scenarios, a secure perimeter created using security measures at the network edge is difficult to achieve and maintain simply because the network edge is no longer a well-defined border but a blurry boundary.
Securing such a dispersed and multifaceted network is where the zero trust model is invaluable.
What is the zero trust security model?
Sometimes referred to as zero trust architecture (ZTA), the zero trust security model operates on the premise of "never trust, always verify."
No user or device should be trusted by default—even if connected directly to the corporate network and even if previously verified. ZTA requires that every transaction that takes place on a network be verified.
ZTA depends heavily on a robust identity verification mechanism to validate a device and a user before granting access to any data or service. This verification is performed whenever a device or a user requests access to some network resource.
Another fundamental principle of ZTA is what is known as the principle of least privilege. It says that each user or device should only be given the smallest amount of privilege, or degree of access, to a service or data required to perform the intended task.
Thus, a user or device can access only the resources for which it has explicit authorization, and each receives only as much access as needed for each transaction.
ZTA provides a granular security mechanism, dynamically providing and revoking access to data and resources as needed.
Once a transaction is complete, privileges to access particular resources are removed until they are explicitly requested once again. At this time, authentication and verification mechanisms will take place again.
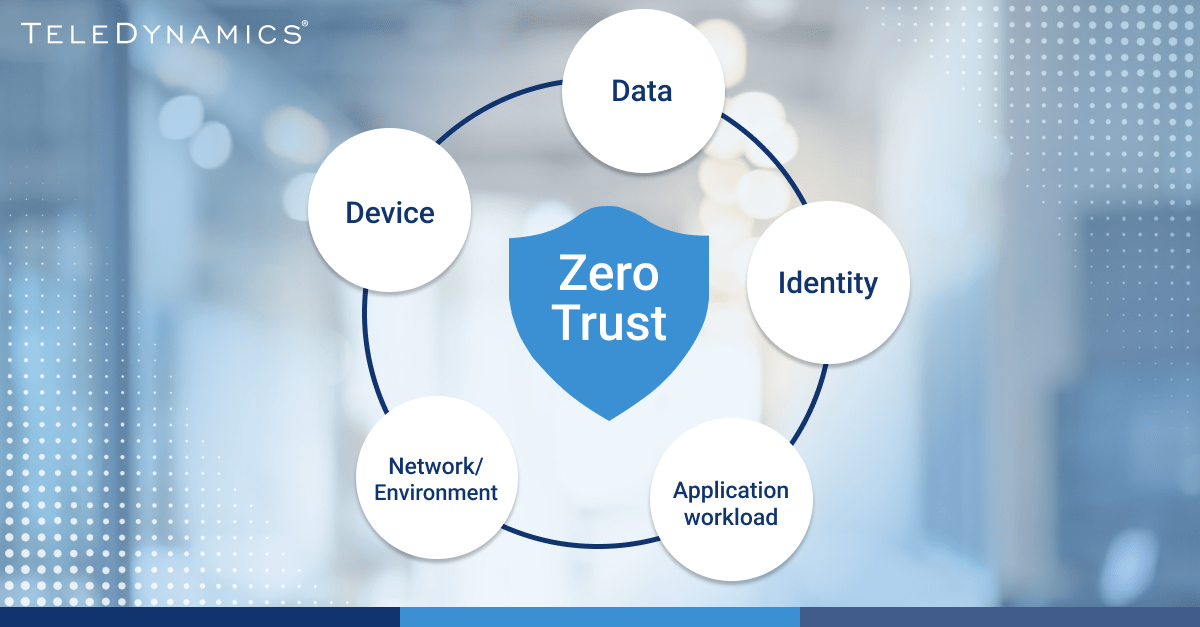
Zero trust pillars
ZTA has yet to be widely deployed, so only a few examples of its implementation in a production network exist. Still, it is receiving much attention from several influential organizations, such as the National Institute of Standards and Technology (NIST) and the National Cybersecurity Center of Excellence (NCCoE), two institutions at the highest level of the U.S. government.
These organizations have jointly published Implementing a Zero Trust Architecture, which describes best practices for ZTA.
Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) has published the Zero Trust Maturity Model, which contains a set of pillars that companies can use as guidelines for proper ZTA deployment. Here is a brief description of these pillars:
- Identity: This pillar deals with verifying the identity of each entity attempting to gain access to a network resource. Identity refers to a set of attributes that uniquely identify a user or device.
Accurately and securely identifying a user or device is central to the ZTA model. It is required to enforce the primary policy that the right users and entities can access the right resources at the right time. - Device: A device is any hardware asset that can connect to the network. This includes devices associated with human users and those that don't correspond to specific users, such as Internet of Things (IoT) devices.
- Network/environment: The network refers to the communications medium that devices use to send and receive, including wired and wireless media and the internet.
- Application workload: This pillar covers the systems, computer programs and services that run on premises or on the cloud. Enterprises should secure and manage these and provide secure application delivery.
- Data: Data refers to any at-rest or in-transit data in a network. Data should be protected in applications, on devices or through communications channels.
UC and zero trust
Unified communications (UC) creates several sessions between client devices and application services. Specific users leverage clients who are authenticated based on their credentials.
Typically, clients may be anywhere where internet connectivity is available. Application services may be located within an on-premises data center, on the cloud, or accessed through native cloud-based subscription services.
The dispersed nature of UC systems makes them next to impossible to secure using a perimeter-based security approach, making zero trust ideal.
For each UC session, ZTA can enhance network security by providing an improved security posture in various ways:
- Secure remote access: Multifactor or two-factor authentication (2FA) is considered to be a core value of zero trust. In ZTA, all connections should require authentication. By definition, authentication should be challenged by prompting users to provide additional proof that they are who they claim to be; for example, by submitting a code received on their mobile device.
- Encryption: Ensuring that all communications are encrypted end to end can provide additional protection against data breaches.
- Application segmentation: By segmenting communications applications into microservices, ZTA can confine the impact of any potential security breaches to a small part of the system.
- Continuous monitoring: ZTA implements continuous monitoring of all network traffic, allowing quick detection and response to any anomalies or suspicious activity.
- Compliance: ZTA can help organizations meet compliance requirements, such as HIPAA or GDPR, by providing greater control and visibility over data access.
Conclusion
The zero trust model is a modern network security approach better suited to modern distributed networks than conventional perimeter-based approaches.
For UC services, zero trust delivers a truly enhanced level of security, ensuring that sensitive voice, video, and collaboration communications are well-secured and remain confidential.
As it becomes more prevalent soon, we can expect UC systems to take advantage of the augmented security benefits that ZTA promises to deliver.
You may also like:
Voice network security and troubleshooting









Comments