
Security is usually one of the top three concerns of most enterprises regarding telecom services. A properly enforced security policy is essential. It can protect against breaches that are capable of threatening organizational viability.
In this article, we share some best practices for creating and maintaining a network security policy and provide an easy-to-use downloadable template to help you create one for your enterprise.
What is a network security policy?
A security policy is a set of well-defined rules and guidelines that define computer network access methods, determine policy enforcement methods and describe the architecture of the organization’s network security environment. These guidelines are both technical and procedural:
- Technical rules: These govern how the policies are enforced within the infrastructure itself. An example might be that remote connections must always access the corporate network using a VPN that supports AES-256 encryption. A policy of this type can be enforced by configuring VPN servers to allow only such connections.
- Procedural guidelines: These deal more specifically with human behavior requirements. An example is specifying that employees may not use their corporate email addresses for personal purposes.
The ultimate goals of a security policy are to protect the organization’s network from malicious attackers outside the enterprise and to exert control over potentially risky internal uses, whether malicious or inadvertent.
The following diagram illustrates the interrelationships among policy, network infrastructure and users.
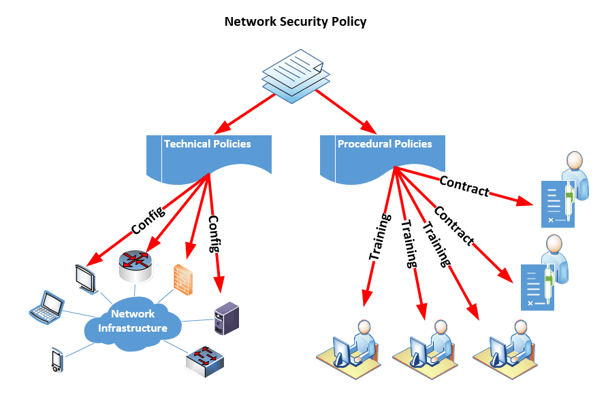
A network security policy starts as a document that specifies all network security guidelines. Technical policies are enforced by configuring the network infrastructure to conform to the required security rules, while procedural policies are enforced by training employees and instituting contractual obligations.
What are the most critical components of a network security policy?
Network security policies can become very complex, especially for larger enterprises that leverage a multitude of services and offer various levels of access and privileges to different users. Because of this complexity, it’s important to organize the policy appropriately. The following is a suggested organizational outline:
- Introduction
- Document scope
- Network infrastructure security
- Network device security policies
- System and server security policies
- Workstation security policies
- Wireless network security policies
- Remote connectivity security policies
- Voice network security policies
- Bring-your-own-device policies
- Physical security policies
- Personal and sensitive information protection
- Procedural security policies
- Online behavior and etiquette
- Other behavioral policies
- Security incident management and reporting
- Additional considerations
This outline is detailed further in our enterprise security policy template, which you can download to give you a head start on authoring a policy for your organization. This is not an exhaustive template, but it provides a perfect starting point for creating your own policy.
Network security tips and best practices
Very few organizations create a complete security policy, and even fewer make one and keep it up to date. While crafting a policy is difficult and requires organizational resources, there are several strategies you can put in place to ensure that yours is an asset to your organization's security.
To create your security policy:
- Assemble a team with the appropriate stakeholders, ensuring that you bring in only those who will be helpful in the process — having the wrong people will often burden the process and make it impossible for the team to get started. Some important people include:
- ICT (information and communications technology) team members
- HR (human resources) representatives
- Members of the legal team
- Separate the policy into sections, and have the appropriate people write brief but intelligible statements describing what is needed. Using a collaborative environment such as Google Docs or a similar cloud-based application can be beneficial here.
- Ensure that the security policy documentation is complete before implementing any policy.
- Once everyone agrees that it is complete, begin applying those policies technically, contractually, or via employee training, as appropriate.
A security policy is a dynamic entity that must be adjusted and adapted based on the changing needs of the organization. To ensure that the policy remains continuously up to date, revisit it periodically, using these tips to streamline the process:
- Have the appropriate stakeholders review the sections that pertain to them monthly or bi-monthly to ensure they still fit current security needs.
- Ensure that any additional services introduced into the enterprise network are accompanied by new sections in the security policy.
- Set aside a half-day annually for all stakeholders to meet and review the policy in its entirety to ensure compliance. Any additional changes should result in modifications of the technical specs of the network, changes in employee contracts and NDAs, and revisions to training programs intended to teach secure practices.
Conclusion
Although an enterprise network security policy requires effort to create and maintain, doing so is essential to ensuring the safety and efficient operation of the organization. That said, drafting the document is not enough to ensure that the organization is protected. Policies must be enforced meticulously at various levels — technical, contractual, and personnel — to gain the most benefit.
You may also like:
Securing VoIP: Systems and network security
VoIP security: Keeping conversations confidential
VoIP security solutions for remote users










Comments