New year, new risks. Let’s talk security.
In today’s digital economy, mobility is not only an expectation, but in many cases, a requirement for workers to successfully fulfill their responsibilities. Security is a key preoccupation for network administrators as they implement voice and data technologies for remote workers.
In this article, we review various remote employee voice service scenarios, look at what their potential risks are, and examine the best voice encryption and VPN solution for each case.
Voice to the remote user
While there are various setups that can be used to provide remote employees with corporate voice services, they all involve a remote voice endpoint in the form of either a SIP client on a device or a physical VoIP phone, and a server that exists on the corporate network that accepts SIP registrations from telephony devices on the internet.
As a result, any properly authenticated VoIP endpoint, whether a mobile device or an IP phone in a home office, can connect to the enterprise network via the internet and obtain an internal corporate extension number. Both incoming and outgoing calls using these devices will occur as if they were physically located within the enterprise network.
Because both voice and control packets traverse an inherently unsecure network – namely, the internet – steps must be taken to ensure the security of these transactions.
Before examining how to protect the VoIP communications of remote employees, let's first look at what kinds of dangers exist.
Risk No. 1: Interception of voice
The most obvious threat to voice communications is the potential for someone to listen in on a conversation. This is not as hard as it may seem, especially if the user is on a Wi-Fi network or on an insecure LAN. This danger exists mostly for the mobile employee that may connect to various shared wired and wireless networks of unknown security during their travels.
For more information, refer to our previous article on Wi-Fi network security.
Risk No. 2: Interception of control communication
An attack of a different kind involves the capturing of SIP packets, the control packets that are exchanged between SIP clients and the SIP server. Registration information such as usernames, passwords, and IP addresses of primary and backup SIP servers can be found in these control packets. This information can be enough for a determined attacker to log in to the corporate network using the extension number of the victim, thus gaining access to all telephony services available to that user.
Risk No. 3: Home office teleworkers
Home office teleworkers are also vulnerable to attacks, but generally to a lesser extent. The most vulnerable points are the SOHO (small office/home office) router – that is, the termination of the internet connection at the home – and the desktop computer itself.
Security solutions
There are several ways to ensure the security of voice communications for remote employees. Which solution to choose has to do with the level of security required, as well as the ease of implementation and administration desired.
All the security solutions described below rely on the tunneling and encryption of voice and control packets using a Virtual Private Network (VPN). There are two factors influencing the effectiveness of a VPN:
- The type of encryption used
- Where the VPN tunnel will be applied
Types of encryption
The type of encryption that will be used depends on the encryption protocol being employed. This, in turn, depends on the protocols that are supported by the devices creating the encrypted tunnel. A brief list of the most commonly used and available protocols for voice applications is shown below. You will find these specified in the data sheets of end devices and related software and equipment.
Point-to-Point Tunneling Protocol (PPTP) – A very common protocol supported by almost all platforms, but which is generally insecure.
IP Security (IPSec) – IPSec is an authentication and encryption suite that uses pre-shared keys for authentication. It is generally regarded as being secure if openly published pre-shared keys are not used. Its built-in compatibility with a large number of devices can make it a beneficial and secure choice if configured correctly. IPSec only applies authentication and encryption, and as such, it must be coupled with a tunneling protocol such as Layer 2 Tunneling Protocol (L2TP) or Internet Key Exchange (IKE) to complete the solution.
Transport Layer Security (TLS) – TLS is a cryptographic protocol with widespread use in many areas of computer networks. TLS on its own can be used to provide authentication and encryption of SIP signaling, but does not deliver voice packet encryption.
OpenVPN – This is considered by most security experts today to be the most complete and comprehensive VPN solution available. This is because OpenVPN is highly configurable and can employ the OpenSSL library and TLS protocols, along with other technologies, to deliver a strong and reliable VPN solution. OpenVPN is also a complete solution because it incorporates both the VPN tunneling mechanism as well as the encryption cipher.
Where the VPN is applied
The second important part of implementation has to do with where the VPN and encryption are applied. Several scenarios are described below. Keep in mind that each scenario can use any of the above-mentioned VPN and encryption algorithms.
Third-party VPN services
This solution is intended for VoIP clients that are installed on mobile devices or desktop or laptop computers. It involves the purchase of a VPN service, the installation of a client on the device in question, and the connection to a particular VPN server somewhere on the internet that acts as a relay between the device and the corporate network. The result is a protected tunnel that is created between the device and the VPN server through which all traffic, including voice traffic, is encrypted. Even if traffic is intercepted, it cannot be deciphered.
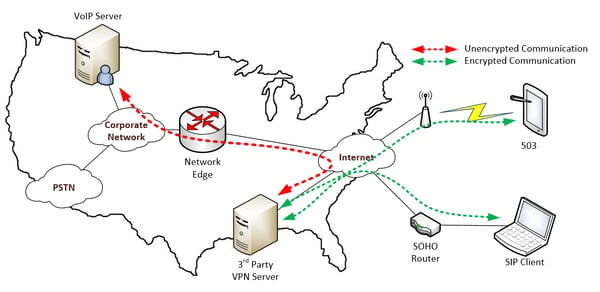
This is an excellent solution for those connecting to the internet via inherently unsecure networks such as public wireless networks, and can also be useful for home employees. It requires minimal technical knowhow to install and configure. Such VPN packages cost as little as two or three dollars per month for each user.
The downside to such a configuration is that the encryption exists only between the device and the VPN server. The second leg of the communication between the VPN server and the corporate network remains unencrypted. This is not so much a concern, as the most vulnerable points of the communication are at the network access points, which are sufficiently covered by this scenario. The other downside is that this solution is not configurable for physical IP phones.
Corporate VPN
This is the complete package for both voice and data. It is essentially the same as the third-party VPN scenario, except that in this case, the VPN server belongs to the corporation and actually resides within the corporate network.
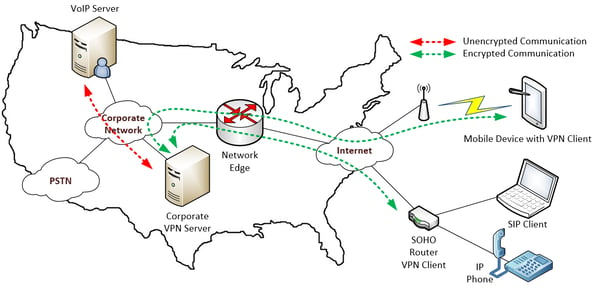
This results in an encrypted tunnel from the device all the way to the corporate network, which of course is more secure. Also, there is the option of either using a VPN client on the device itself, as is the case with the mobile phone in the diagram above, or a VPN router that has a built-in VPN client. In the latter case, all traffic moving between the home and corporate networks, including voice packets from any IP telephone on the home network, will be tunneled and encrypted.
This solution is not trivial to install or procure. It requires technical knowhow to configure, and, depending on the number of concurrent VPN users required, can get somewhat expensive.
VPN to the Phone
Some IP telephony manufacturers have incorporated the implementation of an encrypted VPN tunnel in their IP phones, voice gateways and IP PBXs themselves. This allows for encryption of voice packets between IP phone and IP phone, and between IP phone and gateway, as well as the encryption of control traffic from IP phone to IP PBX.
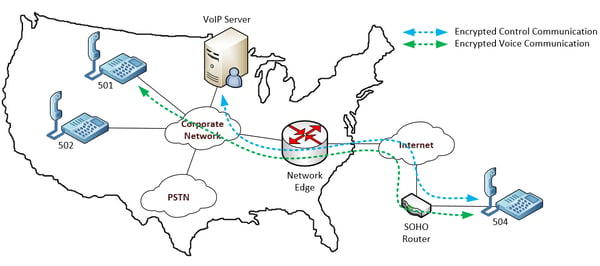
This may indeed be one of the most “plug-and-play” implementations of encryption for voice, since it is already configured in the devices themselves. A quick glance at the data sheet of a device will indicate what security features and protocols it has available.
Be aware, however, that just because phones, gateways, and IP PBXs have some indication of security in their data sheets, it does not necessarily mean that the voice is secure. Security algorithms and ciphers might be mentioned, but these may be only for provisioning or for authentication, and may not actually encrypt the voice and control packets themselves. Verify from documentation or from the vendor directly if necessary, that both voice and data packets are indeed encrypted from end to end in their security implementations.
Conclusion
Security for voice applications used by remote users is an important consideration when providing remote and mobile employees connectivity to the corporate voice network. In general, both OpenVPN and the IPSec security suite are considered to be the most advanced and currently sufficient options for encrypting voice, while TLS is also important, keeping in mind that it only encrypts control packets, not voice packets.
VPN tunnel implementations vary in price, in method and in ease of use. The choice of which to use depends on the particular circumstances of the remote or mobile employees, as well as the corporation’s objectives.
We hope this information will help corporate administrators in their decision-making around security for remote and mobile employees.
You may also like:
How to hack-proof your VoIP network
Is your SIP phone system safe?
For a safe new year, you need more than a firewall









Comments