Unified communications-as-a-service (UCaaS) platforms deliver unprecedented telecom capabilities to modern businesses using cloud-based infrastructure. However, while UCaaS offers a multitude of benefits—such as improved efficiency, scalability, versatility, and reduced costs—it has also become a target for scams and fraud.
Awareness is the first and most crucial step in protecting your business. In this article, we highlight some of the most common attack vectors that these cons attempt to leverage, and we detail how you can secure and protect your network and your workforce from them.
Read More
Topics:
Software Integration,
Network Security,
UCaaS
Product Review
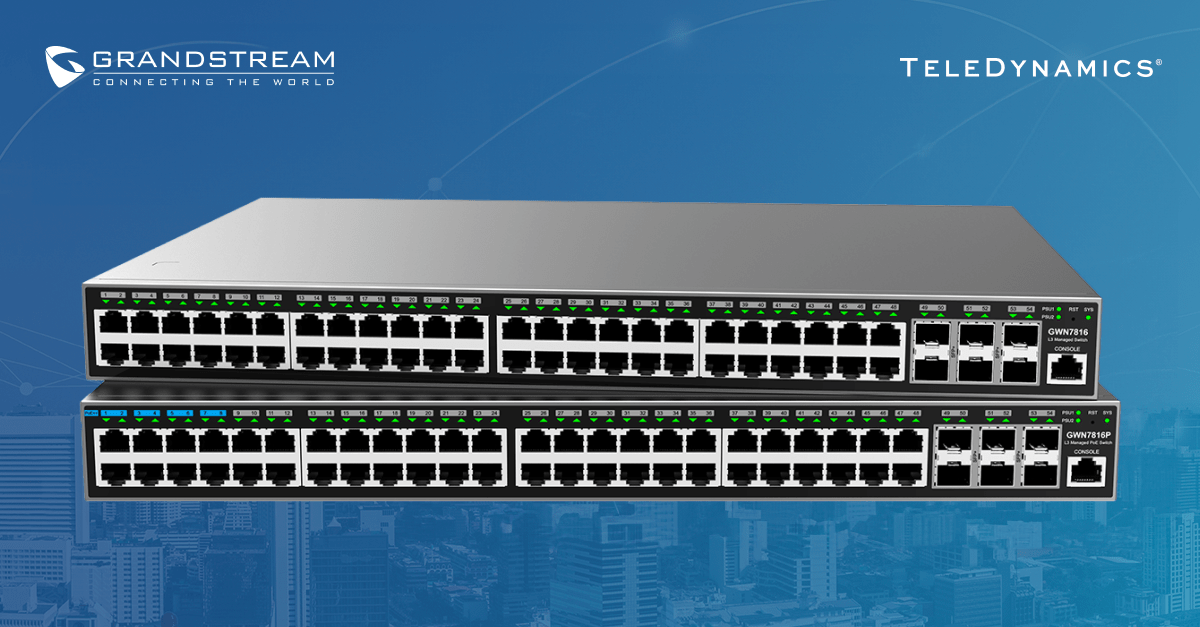
Networks are the lifeblood of modern businesses, and a network is only as effective as the equipment that implements it. Grandstream's GWN7861P network switches are excellent for creating an effective and easy-to-deploy network. This article reviews Grandstream’s 48-port layer 3 managed network switches.
Read More
Topics:
Grandstream,
Network Security,
Product Review,
Switches,
Unified Communications
Unified communications (UC) systems and services increasingly integrate into other network applications, enhancing their overall value and importance. This advancement of UC services impacts the level of complexity involved in their coordination, configuration, integration and operation.
Artificial intelligence (AI) in unified communications is exceptionally well suited to simplify this complexity by implementing smart processes and algorithms to manage these inherent intricacies.
In this article, we explore some of the practical applications of AI within UC, examining functionalities that some have already implemented and some capabilities that we expect in the near and not-so-near future.
Read More
Topics:
VoIP,
Trends,
Network Security,
Troubleshooting,
Unified Communications,
Collaboration,
AI
By Brian Van Meter at Grandstream
Two of the key use cases for a VPN are to connect multiple sites together, such as an enterprise's satellite offices to its central headquarters, and to provide remote workers to a central network so they may access an organization's network resources.
VPNs are widely used throughout business, education, local government, and other deployment verticals that require dispersed locations to be connected together. Within this blog post, we'll be discussing the types of VPNs that you can create with Grandstream's GWN series of routers, and how you can use them to connect workers into one centralized network.
Read More
Topics:
Grandstream,
Network Security,
Routers
As a world-class unified communications equipment and service provider, Yealink takes security seriously. It has made substantial efforts to guarantee that the products and applications it provides its customers comply with some of the most rigorous security standards in the industry.
Yealink has developed enduring relationships with the world's leading component providers in its ongoing effort to maintain high-security levels. This ensures that all its products and applications deliver the utmost in security, reliability, robustness, and usability.
This article looks at Yealink's steps to maintain these relationships, underscoring the company's unwavering commitment to security and compliance.
Read More
Topics:
Yealink,
Network Security,
Videoconferencing,
Communication
Yealink, a leading global provider of unified communications and collaboration solutions, has recently faced some scrutiny due to alleged security concerns about its products and services.
These claims suggest that Yealink products are vulnerable to attacks and may be used by third parties to achieve unauthorized surveillance. As a responsible and thorough investigator of the products we deliver, it is our duty to assess the veracity of these accusations and provide a balanced perspective on the matter.
In this article, we examine the evidence at hand and explore the rigorous security measures implemented by Yealink to ensure the safety and privacy of its users. We hope this helps you understand the issue and make informed decisions about Yealink's products with renewed confidence.
Read More
Topics:
Yealink,
Network Security,
News
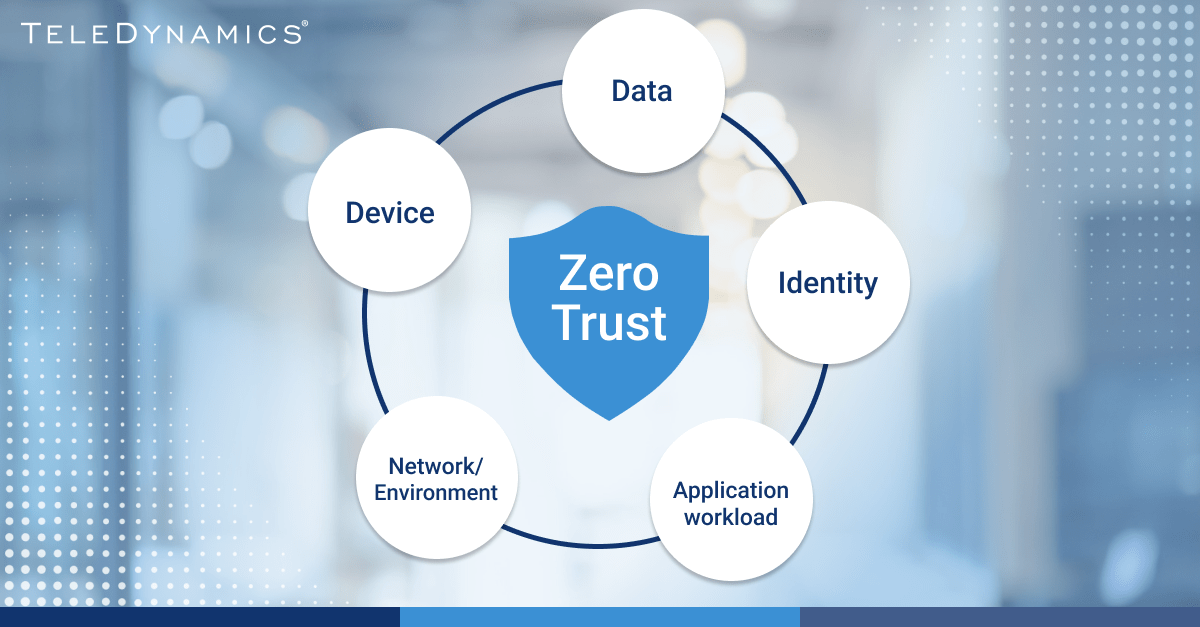
Networks continuously change, and new approaches to security are constantly emerging. One particularly noteworthy approach to network security that has been increasing in adoption over the past couple of years is the zero trust security model.
In this article, we examine what zero trust is, how companies could deploy it over the next few years, and its impact on unified communications applications such as voice, video and collaboration.
Read More
Topics:
Network Security,
Network Design,
Cloud,
Unified Communications
Dealing with voice network security and troubleshooting is an ongoing battle. As new features, capabilities and telecom products emerge, so do potential vulnerabilities and malicious users who may attempt to exploit them. Network and voice administrators must remain vigilant in ensuring security, privacy and confidentiality, which includes staying current with the latest in network troubleshooting and problem resolution.
This article is a review of the important security matters we’ve discussed over the past year, especially when it comes to network security and troubleshooting issues related to telecommunications services.
Read More
Topics:
VoIP,
SIP,
Network Security,
Troubleshooting
Product Review
A key telecommunications trend today involves integrating multiple communications systems that were traditionally implemented separately. IP telephony, video and collaboration, and now security, access and facility management, are all converging into unified communications systems.
Grandstream has recognized and helped further this trend through innovative devices such as the GDS3712 IP video intercom system. In this article, we dig deeper into the capabilities of this device and how its use can simplify and enhance security and facility management.
Read More
Topics:
SIP Phones,
VoIP,
SIP,
Grandstream,
Network Security,
Unified Communications,
Collaboration
Security is usually one of the top three concerns of most enterprises regarding telecom services. A properly enforced security policy is essential. It can protect against breaches that are capable of threatening organizational viability.
In this article, we share some best practices for creating and maintaining a network security policy and provide an easy-to-use downloadable template to help you create one for your enterprise.
Read More
Topics:
Network Security,
Mobile,
Business Strategy,
Regulations,
Collaboration