By Brian Van Meter at Grandstream
Two of the key use cases for a VPN are to connect multiple sites together, such as an enterprise's satellite offices to its central headquarters, and to provide remote workers to a central network so they may access an organization's network resources.
VPNs are widely used throughout business, education, local government, and other deployment verticals that require dispersed locations to be connected together. Within this blog post, we'll be discussing the types of VPNs that you can create with Grandstream's GWN series of routers, and how you can use them to connect workers into one centralized network.
GWN router VPN overview
A virtual private network (VPN) is used to create an encrypted connection enabling users to exchange data across shared or public networks acting as clients connected to a private network. The benefit of using a VPN is to ensure the appropriate level of security for connected systems when the underlying network infrastructure alone cannot provide it.
The most common types of VPNs are remote-access VPNs and site-to-site VPNs. VPNs can be defined between specific endpoints such as IP phones and computers, and servers in separate data centers when security requirements for their exchanges exceed what the enterprise network can deliver.
Increasingly, enterprises use VPNs to secure data and voice exchange. Grandstream GWN7800 routers support several VPN types, enabling installers to create encrypted and tunneled connections across shared or public networks, and allowing users to exchange data securely. These VPN types are:
- OpenVPN: client/server
- IPSec: client/server
- L2TP: client
- PPTP: client
VPN security models mean that client authentication forbids any unauthorized user from accessing the VPN network. Additionally, encryption and confidentiality within the network prevent any "man-in-middle" attacks and eavesdropping on network traffic.
Lastly, VPNs provide data integrity that maintains the consistency and trustworthiness of any packets transferred throughout the exchange. Before users may access a secure VPN tunnel, they must be authenticated. Client/server tunnels use passwords or digital certificates. It is possible to permanently store the certification key, which allows the tunnel to be established automatically for ease of use.
Configuring a site-to-site VPN with OpenVPN
OpenVPN® is a VPN system that offers an open-source Community Edition (CE), and is one of the most popular VPN solutions. It supports both site-to-site or point-to-point connections in routed or bridged configuration and for remote access use cases.
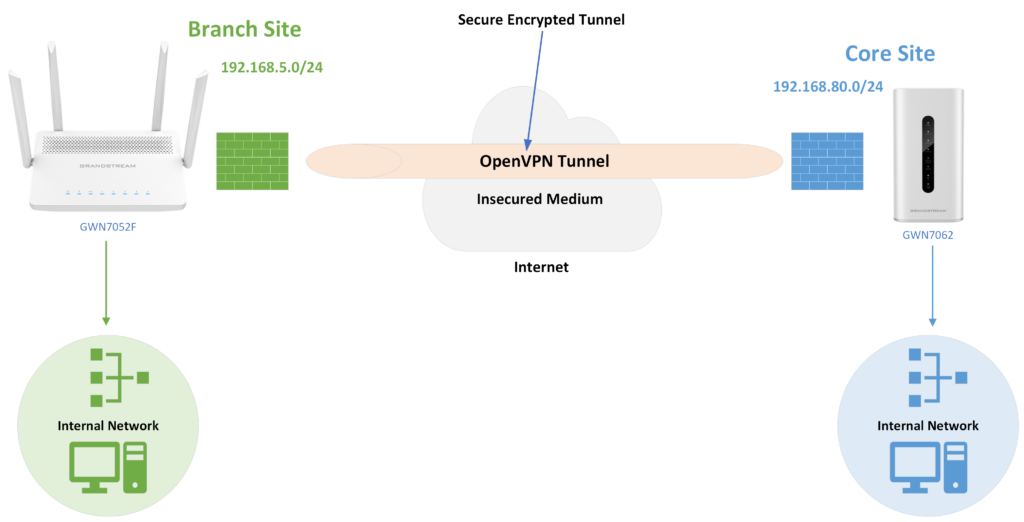
Implementing this solution can be done on both client and server applications. In this example, a client has several branch offices that are connected to the internet using Grandstream GWN7000 series routers. The client would like to establish an encrypted VPN tunnel between the main office location and another branch so it may securely access server assets on the main office network.
Setting up this tunnel will additionally allow VoIP calls to go through the VPN tunnel to prevent potential rogue eavesdropping between the two sites.
- The core site has a LAN subnet with a range of: 192.168.80.0/24 (OpenVPN server)
- The branch site has a LAN subset with a range of: 192.168.5.0/24 (OpenVPN client)
- The VPN tunnel will have the following IP range: 10.0.10.0/24
The figure below shows the actual diagram of the network:
Creating a certificate authority and client/server certificates
- Before configuring the OpenVPN client/server, a certificate authority (CA) and server certificate must be generated, and users added with a client certificate.
- A certificate authority (CA) is a trusted entity that issues electronic documents that verify a digital entity’s identity on the internet. Electronic documents (a.k.a. digital certificates) are an essential part of secure communication and play an important part in the public key infrastructure (PKI).
- Certificates can be created under the GWN router's GUI or through GWN.Cloud/Manager, found under the Systems tab > Certificate Management > Certificate. Certificate customization can be fully configured under this setting menu.
- With a certificate authority created, the next step is to generate the server and client certificates, which can be done within the GUI of the GWN router device or through GWN.Cloud/Manager. This will be assigned to both the server and the client so an encrypted tunnel between the two can be verified.
- For further information on customizing a certificate authority and client/server certificates, take a look at our technical documentation here.
Creating and linking an OpenVPN server
Once client and server certificates have been successfully generated, they are now ready to be assigned and used by the OpenVPN server.
To create a VPN server, navigate to VPN > VPN Server, OpenVPN® Server. Server settings such as the type, name, status, protocol, TLS settings, and more can be configured from this menu option. The server's authentication modes can be accessed within this menu as well, choosing between:
- SSL: Authentication made using certificates only, with no username/password authentication required. This allows for each user to have a unique client configuration that includes their personal certificate and key, which was made earlier. This is typically chosen to provide users with seamless VPN access, however, can be less secure as it does not require the additional security layer of a username and password.
- User Authentication: With this option, authentication is made using only the certificate authority and username and password, meaning no certificates. This setting is useful when creating individual certificates for every user would be an unneeded step, and users can share a TLS key and have their own usernames/passwords.
- SSL + User Authentication: This type of authentication requires both a certificate and username/password. Each user has a unique client configuration, username, and password.
- PSK: This authentication is used to establish a point-to-point OpenVPN® configuration. A VPN tunnel will be created with a server endpoint of a specified IP and a client endpoint of a specified IP. Encrypted communication between client and server will occur over UDP port 1194, which is the default OpenVPN® port. This method is incredibly secure, as there are multiple factors of authentication, TLS Key, Certificate, and username and password.
The final step in server creation is to allow it on the desired network grounds. This is done by editing created VLANs and setting the new server as a desired Destination. With this finish, the OpenVPN® client can be configured on the GWN router at any branch site that needs to be connected to the central site.
This can be done through the router's GUI or through GWN.Cloud/Manager through the VPN > VPN Clients menu option. The same as the OpenVPN® Server, make sure to allow OpenVPN® Client on the desired network groups.
Configuring a L2TP client VPN
Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the delivery of services by ISPs. It does not provide any encryption or confidentiality by itself. Rather, it relies on an encryption protocol that it passes within the tunnel to provide privacy.
L2TP deployments are typically deployed alongside other technologies, such as IPSec, to provide encryption and authentication capabilities. L2TP is most frequently deployed as a remote-access VPN, providing remote users who are working from a home office or traveling with access to a centralized network.
L2TP configuration on a GWN router is fairly straightforward, requiring the server information, username, and password of the VPN Server configuration when adding the VPN client.
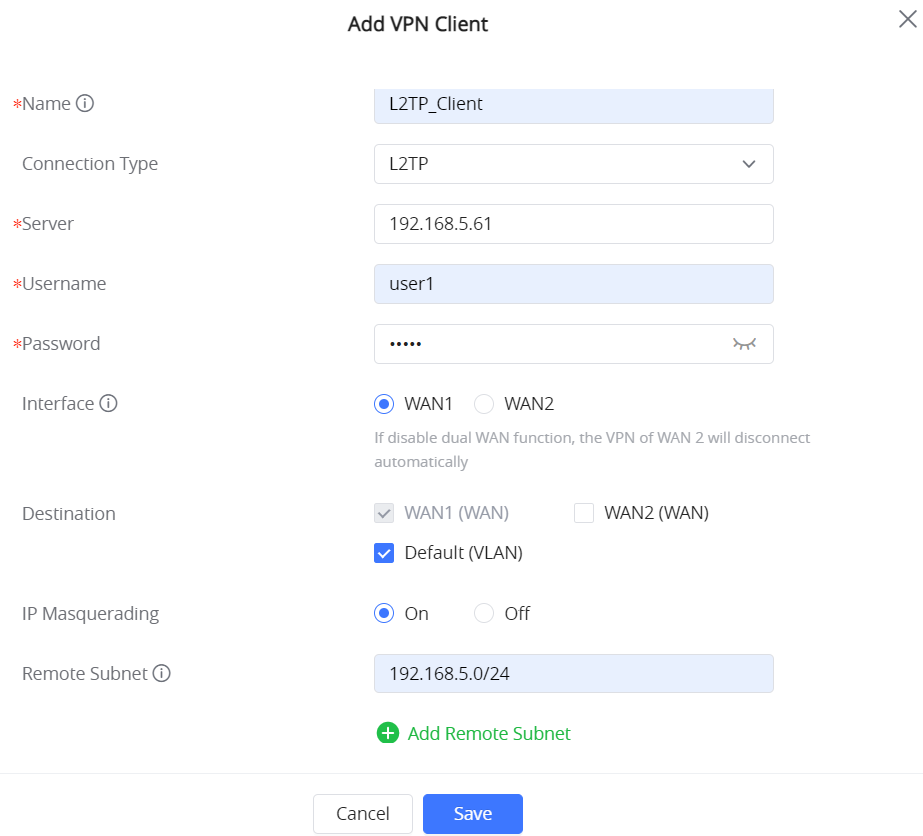
For more information on configuring an L2TP client VPN on GWN routers, visit our technical documentation here.
Configuring a PPTP VPN
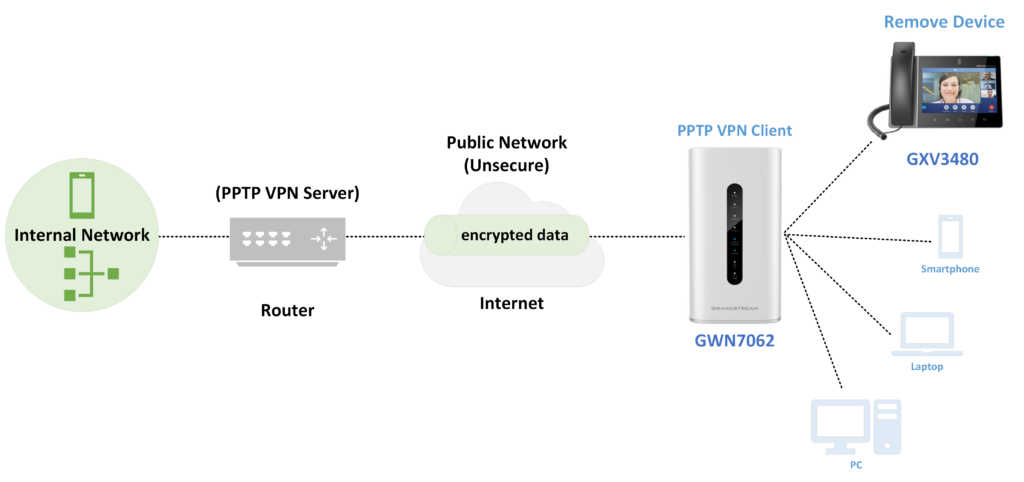
PPTP is a data-link layer protocol for wide area networks (WANs) based on the Point-to-Point Protocol (PPP) and developed by Microsoft that enables network traffic to be encapsulated and routed over an unsecured public network such as the internet.
Point-to-Point Tunneling Protocol (PPTP) allows the creation of virtual private networks (VPNs), which tunnel TCP/IP traffic through the internet. GWN70xx routers support PPTP client VPN; the created VPN can be associated with a VLAN, so all the devices connected to the router will use the VPN tunnel.
Please refer to the figure below.
The first step to creating the PPTP VPN is to create and configure the PPTP server parameters. It is important to note that the PPTP Server address needs to be the same as on our PPTP Client. Other settings such as PPE, forwarding between sites, traffic routing policies, and other parameters can be edited from the GWN routers GUI or GWN.Cloud/Manager.
Once server setup is completed, PPTP user credentials must be created in order to allow them to connect to the PPTP server. PPTP user creation is a straightforward process, only requiring the full name of the user, a related username, and a password. These will be used for configuring the PPTP Client in the following step.
With PPTP Users created, the next step is to begin configuring the clients, which can be done in the VPN Clients submenu of the GWN router. When creating a new VPN client, the username and password that were set previously in the PPTP user creation set must be input here. Finally, the PPTP Client VPN must be enabled on the desired VLANs.
More on Grandstream GWN router VPNs
VPNs are the ideal way to securely connect two geographically separated locations and are frequently used for branch offices, remote workers, and other site-to-site deployments. Grandstream's GWN series of routers are robust solutions that can do much more than create VPNs. To take a deep technical dive into their capabilities, you can visit our Documentation Center page.
Interested in learning more about creating VPNs? In one of our latest Video Guides, our support team created a step-by-step guide on customizing an OpenVPN®.
Note: This article was originally published on Grandstream's blog. Browse the TeleDynamics website for Grandstream products.
You may also like:
Grandstream GWN7661: Superior Wi-Fi for homes, hotels, and everything in between
How to create VLANs with Grandstream GWN7800 series switches
Grandstream GWN7052(F) Wi-Fi router product review








Comments