
If you’re on the voice side of the telecommunications industry, it is inevitable that you will be dealing with data networking. As Voice over IP (VoIP) technologies are overtaking more traditional telephony systems such as ISDN and analog, the voice engineer is required to know data networking fundamentals in order to implement, maintain and troubleshoot modern voice systems.
Back in 1999, when VoIP was still in its infancy, Industry Expert Bruce Robertson told students in the Sheridan College Telecommunications Management post graduate program, “If you go into the telecom industry on the data side, you will probably stay on the data side for all of your career. If you go in on the voice side of things, you will inevitably become involved with the data side, as well.”
This statement has certainly borne true. So, if you’re an expert in ISDN, SS7 or other conventional telephony technologies, it’s essential to also be familiar with data networking fundamentals to remain competitive and relevant in the telecom industry. In this article we look at a nifty tool called a packet sniffer that can be used for troubleshooting many types of VoIP problems and should be in the toolbox of any telephone installer.
The nature of conventional voice compared with VoIP
The troubleshooting procedures for any kind of application that is running on an IP network are quite different from those involved in traditional telephony. Traditional voice is primarily circuit switched, which means that connections are made from end to end whenever a call is initiated, and are torn down once the call is complete. This is true even of ISDN circuits, which operate in a similar manner even though they are digital.
VoIP, on the other hand, which takes advantage of IP networks, is packet switched. This means that the voice of a caller being transmitted over the network infrastructure is broken down into small pieces or packets that are sent individually. Packets may take various paths to get to their destination, where they are reassembled into the original voice conversation.
This fundamental difference profoundly affects how troubleshooting is approached in each case. Troubleshooting experience and techniques used in conventional telephony are of limited value when applied to VoIP.
Network troubleshooting tools and techniques
For this reason, it is important to approach VoIP troubleshooting from the point of view of data networks. Data networking professionals have a number of tools at their disposal to diagnose and resolve problems on the network, and these can be useful for voice engineers, as well. One of the most fundamentally useful and diversely applicable tools is a packet sniffer.
A packet sniffer is a piece of software running on a computer that can capture and analyze packets traversing the network. Once captured, these packets can be examined, and many problems can be investigated using the information found within them. A packet sniffer essentially presents a glimpse into the inner workings of a network session, such as a VoIP conversation.
VoIP packetizes voice to send it over the network. Even control information exchanged between VoIP end devices and an IP PBX using Session Initiation Protocol (SIP) are packetized and transmitted in the same way. This makes a packet sniffer an ideal tool for troubleshooting voice issues.
There are various packet sniffers available today. The two most commonly used are tcpdump, a command line packet analyzer primarily available for Unix-based systems, and Wireshark, an application that provides a graphical user interface which is available for Windows, Mac, and some Unix-like operating systems. Wireshark is a free and open source packet analyzer and is used by the majority of networking professionals today. One could say that it has become the de facto industry standard for packet analyzers. In this article, we’ll be focusing on Wireshark.
How does a packet sniffer work?
A packet sniffer that is installed on a computer is able to detect, capture and save packets that traverse the computer’s network card, either inbound or outbound. These packets are collected and decoded so that the raw data they carry can be viewed, including the values of various fields such as source and destination MAC addresses, source and destination IP addresses, as well as source and destination Transport Layer ports.
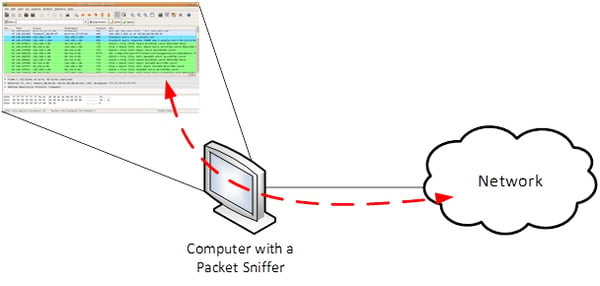
As shown in the image above, all traffic traversing the network card of the computer in either direction is captured by the packet sniffer. This is ideal for troubleshooting problems that involve specific applications running on the very same computer, such as a softphone or a SIP client. For situations where you want to examine traffic that is being exchanged between other devices on the network, you can use Wireshark in promiscuous mode.
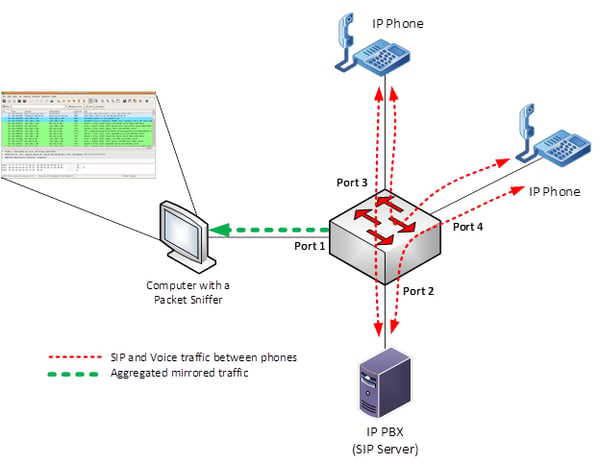
Wireshark has the ability to read and capture packets that are not destined for the computer it is running on. However, in order to do this, Wireshark must be configured to detect those packets and include them in the capture. The configuration parameter that does this is called promiscuous mode. This mode reads and records all the packets that arrive on the interface, regardless of the actual intended recipient of that data. The only prerequisite is that the monitoring computer must be on the same network segment or VLAN as the devices generating the traffic to be analyzed.
Wireshark requirements
Let’s say you’ve enabled promiscuous mode, you’ve plugged the management computer in the proper destination port and you’re ready to start sniffing packets. What do you need to do in order to get Wireshark to operate correctly? Here is a brief checklist of information to keep in mind. This checklist is oriented more for Windows users, although it is similar for other platforms, as well.
WinPcap
In order for Wireshark – or any other packet analyzer – to correctly sniff, store and display packet information, it must conform to a packet capture library. Without getting into too much technical detail, a packet capture library essentially defines the format in which the packets will be captured and displayed. It is also responsible for providing the network card with the capability of capturing packets on the interface. WinPcap is a Windows service that must be installed and running on the computer that is actively sniffing packets. To simplify things, Wireshark automatically installs the WinPcap utility during its own installation process, and when you start Wireshark, it lets you know if the service isn’t running.
.pcap files
When packets are captured, they are not stored as separate entities on the computer, but rather are kept in a container file called a packet capture or .pcap file. These are files that can be saved and read using Wireshark or other packet sniffers that conform to the .pcap format. These can be saved, shared and reopened for analysis just like you would any other file on your computer.
Capturing packets
Because high-traffic network connections can often have thousands of packets per second traversing them, it is impractical to have a packet sniffer actively sniffing for long periods of time. .pcap files can quickly become very large, and needlessly so. Wireshark has a start/stop button that you can click to start and stop capturing packets whenever you like. Start the packet capture, have the applications you are testing begin to generate traffic, and after a few seconds, stop the capture. You can see the packets appear on the screen as rows of a table similar to what is shown in the screenshot below.
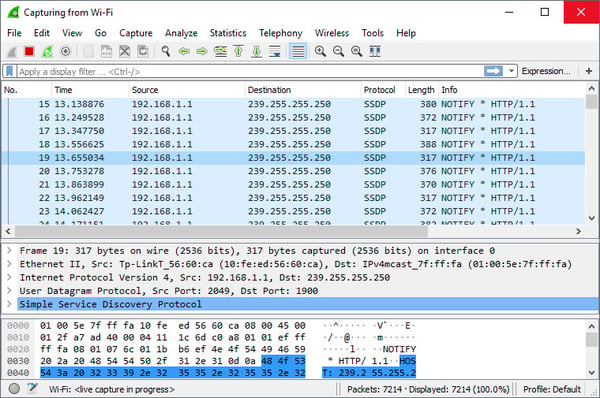
So, in a real-world example where you are testing to see traffic between two IP phones, you would start the capture, initiate a call, terminate the call and then stop the capture. The whole capture process should not take longer than a few seconds. Just make sure that you’ve captured the packets during the full duration of the process you are testing.
Displaying captured packets
Once the packets are captured, they are displayed in a table-like format where each row corresponds to a single packet, with information such as source and destination IP, and the Transport Layer protocols being used. You can click on a row to view more detailed information about the packet including the Data Link Layer (Ethernet), the Network Layer (IP) and Transport Layer. For other protocols like SIP, an additional layer is displayed above the Transport Layer that includes information specific to voice conversations. For SIP and telephony issues, the most important part of the packet to examine is this SIP entry, and to a lesser extent, the Transport Layer.
Step-by-Step guide to Wireshark
If you'd like more detail or clarification, you can download our free guide that more thoroughly explains the basics of Wireshark and shows how to use it for troubleshooting voice issues on a network.
CONCLUSION
To keep up with pace of technological advancements, voice engineers are required to understand the IP networking world. Learning Wireshark is an important step in that direction, and will help in troubleshooting many of the most common issues faced by voice engineers when implementing VoIP technologies.
You may also like:
How to resolve one-way or no-way audio on VoIP calls
Common VoIP issues and how to fix them
How to troubleshoot one-way and no-way audio on VoIP calls










Comments