
Voice over IP networks can be challenging to implement efficiently and securely. This is in part because voice packets require specialized management and must be treated differently than normal data packets. Quality of Service (QoS), security and flow control are just some areas in which the required handling of voice traffic differs from conventional data traffic.
The good thing is that with the proper expertise and care, many of these issues can be successfully dealt with within the corporate network. Such networks are under the complete control of the network administration team and thus can be fully customized for the needs of the voice being transmitted.
However, what happens when voice packets are routed beyond the corporate network, either for voice calls to the PSTN or mobile network, or for employees who use internal voice network services remotely? Here we look at various network edge mechanisms that can be used to monitor and manage data traveling in and out of the LAN.
A Voice over IP gateway or media gateway is one of the most basic edge devices used for voice traffic. Its primary purpose is to translate voice from one technology to another – from ISDN to VoIP or from analog PSTN to VoIP. Additional functionalities can include routing calls between gateways, as well as connecting to external controllers such as gatekeepers or network management systems. To learn more about media gateways and see side-by-side comparisons of different manufacturers, refer to TeleDynamics’ Ultimate Guide to Gateways.
Firewall is a device whose primary purpose is to protect the internal network from external malicious attacks. Based on specific configurations, packets coming from the internet are either allowed to pass or blocked. Advanced devices known as second- and third-generation firewalls can perform what is called deep packet inspection which can determine not only the port numbers and IP addresses of the sender but also the nature of the packets being sent. This includes identifying a packet as part of a voice conversation, an email, a web page or a file transfer. Based on these detailed elements, the firewall can make an informed decision as to whether or not it is safe to allow a packet into the corporate network. These devices have specialized features that accommodate the special nature of voice packets to more effectively manage security on the edge.
A Session Border Controller or SBC (in an enterprise setting, it is also called an ESBC) is a specialized device that sits on the edge of the voice network and whose purpose is to protect the private telephony network from malicious attacks such as Denial-of-Service (DoS) and toll fraud. An SBC can do this by exerting control over the signaling (i.e. call setup and teardown) as well as the media streams – that is, the actual voice packets of IP telephone calls. It also provides functionalities that allow for the simple and secure provisioning of internal services to mobile employees via techniques such as NAT traversal, SIP message and header manipulation and VPN connectivity. Additional features include IPv4 to IPv6 interworking, QoS benefits as well as VoIP protocol translations between SIP, H.323 and other proprietary protocols. For a more in-depth look at SBCs, refer to our previous article, Five reasons you should add an SBC to your IP network.
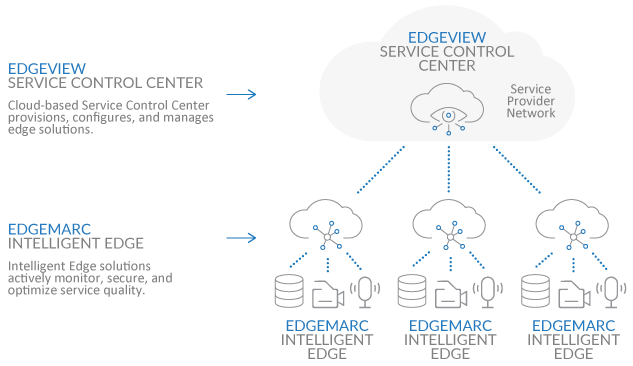
Software Defined Networking or SDN is not a device, but an approach to computer networking that provides network administrators with the capability of dynamically adjusting, controlling and managing the behavior of a network to accommodate the continually changing needs and requirements of the traffic being transmitted. Also known as Network Edge Orchestration or Network Services Orchestration by some major vendors on the market, it is more of a network architecture than a series of products. The SDN philosophy states that static network architecture does not adequately address the dynamic needs of modern networks as far as fluctuating traffic volume, security needs, quality of service and flow control are concerned. When applied to the network edge, an SDN inspired architecture can dynamically adapt to the needs of all types of traffic including both voice and data.
This is achieved with the use of a cloud controller that allows for the centralized management of all associated network devices. Administrators implement high-level policies on the controller that are intelligently interpreted. Appropriately crafted configurations are then pushed to the network devices, which continually communicate with the controller and inform it of changes in network behavior. The controller in turn dynamically updates the network devices on how they should behave based on the policies implemented by the administrator.
This allows for a centrally managed, adaptable, agile and flexible network management functionality that can benefit the performance and security of both voice and data traffic at the edge of the network.
CONCLUSION
There are various methods for providing a secure and effective network edge for both voice and data traffic. The choice of one or a combination of several solutions depends on the specific needs of the network in question. The most important thing is to adopt an overall network architecture that meets the enterprise objectives and to choose devices that not only optimize voice traffic, but also effectively serve the converged network as a whole.
You may also like:
What network convergence can do for your company
Time-saving telephone network installation tips
For a safe new year, you need more than a firewall









Comments