
One of the best methods for troubleshooting problems on the network to pinpoint the cause of poor voice quality or a disruption of VoIP services is to capture voice packets in real time and store them so we can analyze them later. When people call TeleDynamics tech support, we sometimes ask them to show us their packet capture files so we can help identify the issue. In this article, we examine practical methods for capturing voice packets at various locations within the network.
Capturing packets
Unless you have a sophisticated network monitoring system that observes and records events on the network, it is unlikely that you will have in your infrastructure direct and immediate access to any pertinent information concerning the flow of voice packets. So, when voice degradation strikes, one of the first things you should do to determine the cause of the issue is capture packets at strategic locations within your network. How to choose the location of capture is something that we covered in our recent article on troubleshooting poor voice quality and will not be elaborated upon here. Instead, here we look at the practical aspects of capturing voice packets.
Process
In order to capture packets, several things are required:
- First, a monitoring computer running packet capture and analysis software. In most cases, this would be a laptop running Wireshark.
- Next, you need an entry point onto the network that will allow you to connect the laptop to capture the packets.
- Finally, a configuration of the network equipment so that packets can be sent to the monitoring computer for capture and storage.
Monitoring computer
Wireshark can be downloaded and installed on any Windows or Mac computer for free. Its installation is quick and simple, and its operation is quite intuitive. The use of a laptop is advantageous because you may need to monitor your network at various locations, so being mobile enough to move from data room to data room is important. We go into detail about Wireshark and how to use it in our free guide to troubleshooting VoIP issues using Wireshark.
Preparing the entry point
What we have been calling the “entry point” until now is simply a specially configured Ethernet port on some network device to which the monitoring computer can be connected. Such a port can be configured at several locations. It could either be on a network switch to which both PCs and IP phones connect, or it could be on an IP phone itself. Both scenarios are described below.
Port mirroring
Port mirroring is a feature included with most brands of managed switches. It is used to copy incoming and outgoing packets from multiple ports of that switch and output them to a single port. The ports whose traffic is copied are called source ports, and the port to which the copied packets are sent is called the destination port. The monitoring computer is connected to the destination port, from which it receives all of the mirrored traffic. This destination port is what we, until now, have been referring to as the entry point. The following diagram depicts the operation of port mirroring on a switch.
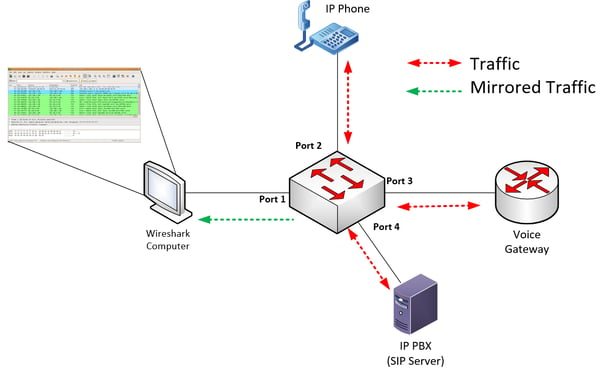
Note in the above diagram that such a configuration will allow you to capture packets to and from any VoIP device connected to the switch including IP Phones, voice gateways, and IP PBXs. This is especially useful when your troubleshooting procedure requires you to examine both SIP control traffic as well as the voice packets themselves at multiple physical points on a network.
Some points to keep in mind when configuring port mirroring include:
- Although voice traffic generally uses very little bandwidth, there is other traffic on the network as well, and packet capture files can get very big, very quickly. Therefore, packet capture intervals should be kept to a minimum.
- Be careful not to oversubscribe the destination port by monitoring too many source ports. This could result in losing some packets, as well as in a degradation in network performance.
- The mirroring feature uses extra CPU and memory resources and should be used with caution on production networks.
- The port mirroring process itself will not affect any of the traffic to and from the devices connected to the source ports.
- While this may vary among switch vendors, the monitoring computer connected to the destination port will typically not have network access, so connectivity to the internet or to other network resources will not be available to that computer.
Monitoring at an IP phone
Most IP phones today sport a second Ethernet port, enabling you to connect both a phone and a PC to a single switch port. Some higher-end phones have the capability of providing a voice packet monitoring service to this Ethernet port that mirrors voice packets to the connected PC. This configuration is shown in detail below.
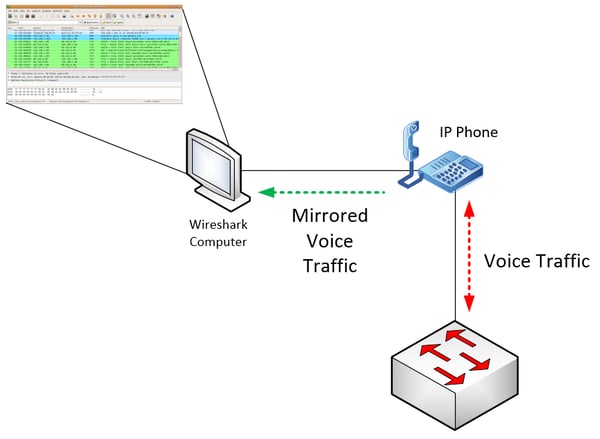
In such a scenario, the phone itself must support this feature and must be configured to mirror traffic from one Ethernet port to the other. If you install Wireshark on the connected PC, you can capture and analyze the mirrored voice packets that are exchanged between the phone and the switch.
If the phone manufacturer does not support this feature, you can employ the following hack using an old Ethernet hub. Unlike a switch, a hub will take all frames inputted on one port and send them out of all other ports. Small five- or eight-port hubs are still available on the market, so you can still get a hold of one if you don’t have one. Externally, a hub will look the same as a switch, so make sure that it says “hub” on the label!
With the hub, create a topology similar to the following:
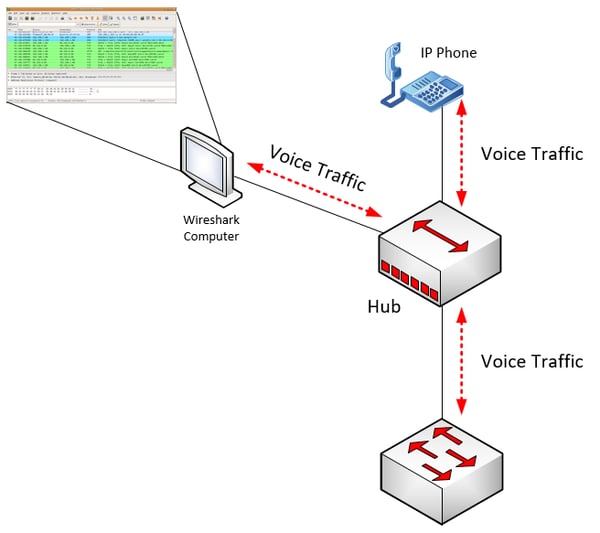
A hub doesn’t need to be (and actually cannot be) configured like a switch for the mirroring feature, because this is the way a hub operates by definition. The result is that any voice traffic going to and from the IP phone will be automatically replicated and sent to the monitoring computer.
Filtering captured packets
As you can see, with the processes we’ve described, all data packets, whether they be for signaling, voice, or data, will be captured and “dumped” to the destination port and onto the monitoring computer for capture. How on earth are you going to be able to sort through so many millions of packets to find the few you need to proceed with your troubleshooting? This is where the power of packet sniffers like Wireshark comes in. Packet sniffers are able to efficiently parse through the captured packets and pick out those of a particular voice conversation and display them on the screen. Powerful filtering processes are employed to show the troubleshooter the relevant information while filtering out all of the unneeded noise. More about how to use these powerful features can be found in our free guide to troubleshooting VoIP issues using Wireshark.
Conclusion
When problems arise on the network, knowing how to capture packet packet flows for analysis is essential, especially when dealing with VoIP issues. This allows you to get to the root of the problem as quickly as possible, and have it diagnosed and solved in the least amount of time.
You may also like:
Using Wireshark to troubleshoot VoIP
Troubleshooting poor voice quality on VoIP systems
The advantages of SDN for VoIP









Comments